The ALPHV/BlackCat ransomware gang filed a regulatory disclosure related to a material cybersecurity incident affecting its victim, MeridianLink, on Wednesday, November 15, 2023. The group used the U.S. Securities and Exchange Commission’s (SEC) Tips, Complaints, and Referrals page to file a complaint alleging that their victim failed to disclose a “significant breach” via a Form 8-K filing as required by recently adopted cybersecurity disclosure requirements.
MeridianLink Suffers November 7 Ransomware Attack
The ransomware group added MeridianLink to their leak site on November 15, the same day they filed the SEC complaint, according to BleepingComputer. An ALPHV source told DataBreaches.net that the attack occurred on November 7th and that the victim’s files were not encrypted, but rather exfiltrated.
MeridianLink (NYSE:MLNK) is a publicly traded company that provides technology solutions that “empower financial institutions to develop lifelong financial management relationships to support a customer’s entire financial journey.” The company products include a digital lending platform and loan origination system for financial institutions.
MeridianLink was aware of the attack on November 7, and ALPHV allegedly told DataBreaches.net that the company did not make any security upgrades immediately following the discovery of the breach. However, the gang said, “once we added [MeridianLink] to the blog, they have patched the way used to get in.”
SEC Adopts July 2023 Cybersecurity Disclosure Rules
The U.S. Securities and Exchange Commission adopted new rules on cybersecurity governance, risk, and compliance (GRC) and incident disclosure by public companies in July 2023. The rules were published to the Federal Register on August 4, 2023 and went into effect 30 days later on September 5, 2023.
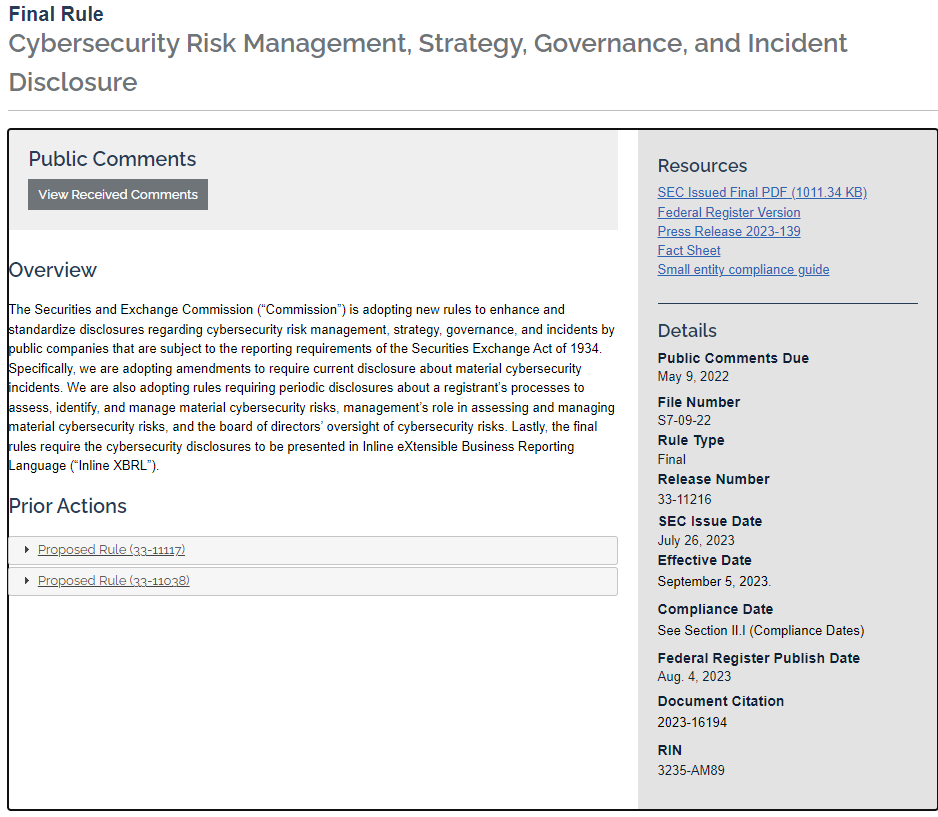
According to a July 26, 2023 official SEC communication, the civil enforcement body now requires “registrants to disclose material cybersecurity incidents they experience and to disclose on an annual basis material information regarding their cybersecurity risk management, strategy, and governance.”
The new cybersecurity disclosure requirements apply to public companies that are “subject to the reporting requirements of the Securities Exchange Act of 1934.” The final rule goes into effect as ransomware attacks and other cybersecurity breaches have increased in frequency and magnitude in recent years.
Many articles, including one by Thomson Reuters’ Senior Regulatory Intelligence Specialist, Todd Ehret, have incorrectly claimed that the rules do not go into effect until December 15, 2023.
ALPHV is a Sophisticated and Active Ransomware Gang

ALPHV/BlackCat is currently one of the most active ransomware gangs in the world. While it has been on the radar of cybersecurity professionals and threat hunters for some time, the group achieved mainstream notoriety following its September 2023 vishing attack against MGM Resorts International which crippled the casino and hotel chain’s operations for weeks.

The MGM Resorts ransomware attack took several systems offline, including check-in, check-out, ATM machines, slot machines, merchant processing, rewards systems, parking garages, and digital room keys. As of September 18th, large blocks of slot machines remained offline. Pursuant to the new cybersecurity disclosure requirements, MGM Resorts stated in an October 5th Form 8-K filing with the SEC, that the attack resulted in an estimated “negative impact” of “approximately $100 million to Adjusted Property EBITDAR.”

According to Twitter (X) user @CyberSleuth1, “ALPHV has characteristically been very a silent group which makes it difficult to create biographies on their members. Some of their affiliates are sloppy but the actual group members are quiet and their operations are more sophisticated than most ransomware groups. They have breached a couple of defense contractors, which is what brought them into the [Central Intelligence] Agency’s scope.”
@CyberSleuth1’s Twitter (X) bio indicates that they are retired National Security Agency, U.S. Cyber Command, Cyber National Mission Force, and U.S. Space Command, and currently monitoring cyber events and “#ThreatIntelligence.” They have previously provided cyberintel.xyz with comments on the MGM Resorts ransomware attack.
ALPHV Files SEC Cybersecurity Disclosure Complaint Against MerdianLink
The SEC’s EDGAR database for reporting companies’ filings shows that MeridianLink has not filed any documents since filing a Form 4 (Insider Trading Report) and Form 144/A (Sale of Securities) on November 9. The Form 4 filing indicates that the company’s Chief Financial Officer, Sean Blitchok, sold 16,789 shares of common stock at a price of $18.5138 per share for a total of $310,828.18 on November 8, just one day after the company allegedly discovered the breach.
If Blitchok was aware of the cyberattack prior to executing this trade, he may have committed securities fraud by trading on material non-public information. However, the gains would be negligible, as the company’s stock price has remained relatively stagnant over the past 10 days.
Based on the SEC’s new cybersecurity disclosure rules, MeridianLink had until November 13, 2023 to file a Form 8-K regarding the ransomware attack. On November 15, 2023, ALPHV published screenshots of their SEC complaint to their leak site, according to BleepingComputer.
Full text of ALPHV’s post on its leak site:
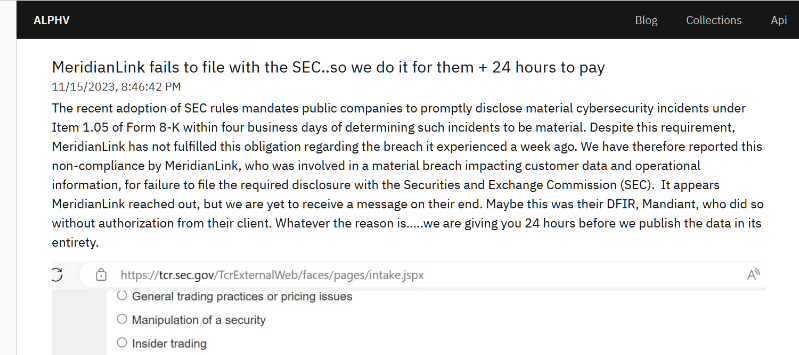
“The recent adoption of SEC rules mandates public companies to promptly disclose material cybersecurity incidents under Item 1.05 of Form 8-K within four business days of determining such incidents to be material. Despite this requirement, MeridianLink has not fulfilled this obligation regarding the breach it experienced a week ago. We have therefore reported this non-compliance by MeridianLink, who was involved in a material breach impacting customer data and operational information, for failure to file the required disclosure with the Securities and Exchange Commission (SEC). It appears MeridianLink reached out, but we are yet to receive a message on their end. Maybe this was their DFIR, Mandiant, who did so without authorization from their client. Whatever the reason……we are giving you 24 hours before we publish the data in its entirety.
“
How much credibility will the SEC give to this complaint from a cybercriminal organization?
Twitter (X) User, @CyberSleuth1
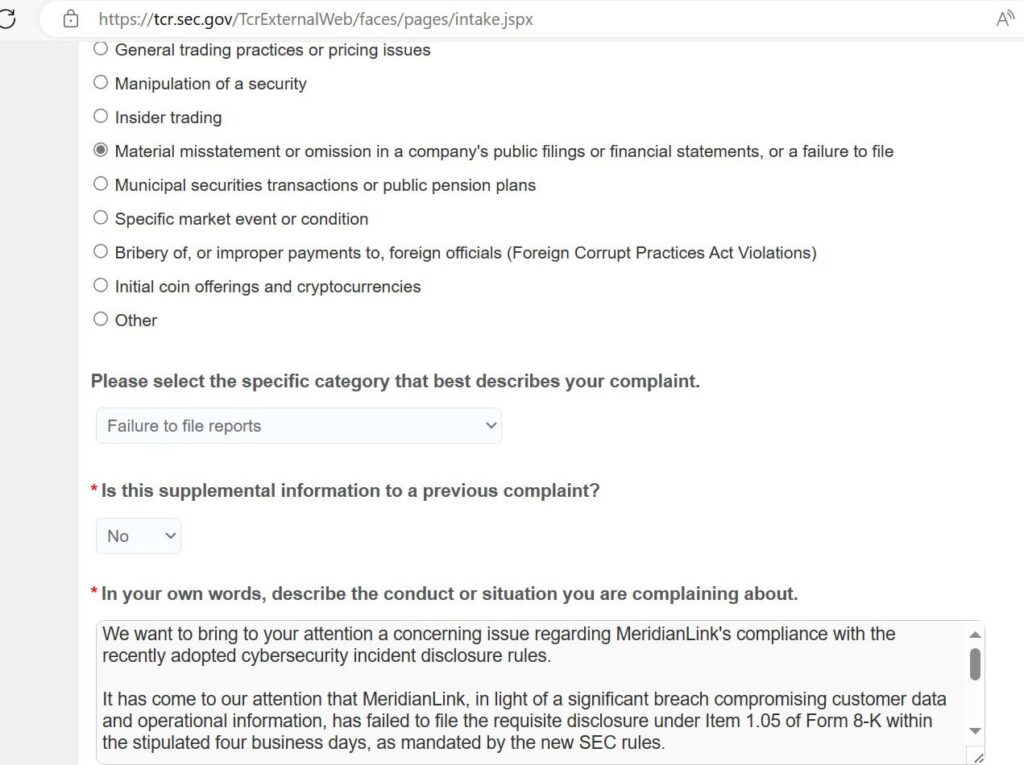
Based on the screenshot, the ransomware gang’s complaint read, “We want to bring to your attention a concerning issue regarding MeridianLink’s compliance with the recently adopted cybersecurity incident disclosure rules.” It continued, “It has come to our attention that MeridianLink, in light of a significant breach compromising customer data and operational information, has failed to file the requisite disclosure under Item 1.05 of Form 8-K within the stipulated four business days, as mandate by the new SEC rules.”
For security reasons, cyberintel.xyz could not review the authenticity of these posts or ALPHV/BlackCat’s leak site.
“People think this is the first time a ransomware group is trying to use legal entities to influence their ransom payments,” @CyberSleuth1 said. “This is an extortion tactic that won’t work. I’ve seen a lot of people discussing this as the first-ever type of extortion tactic. Snatch ransomware group has been using a similar tactic since early August.”
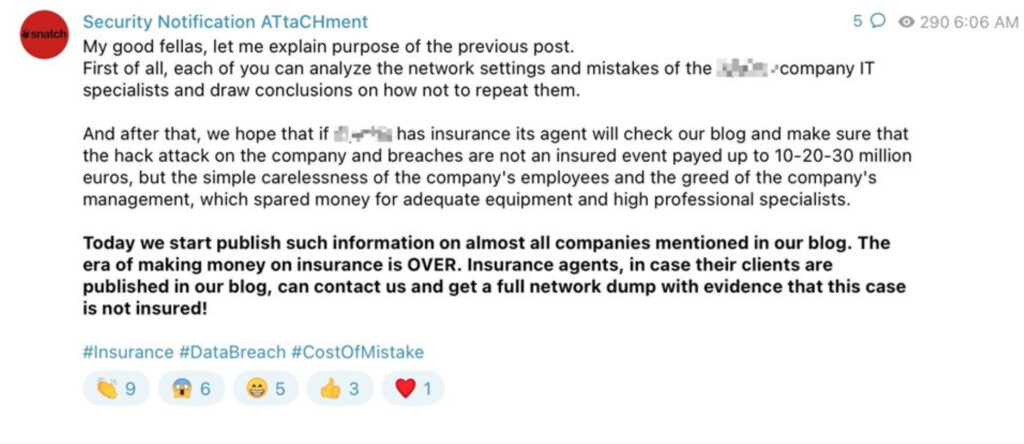
Expanding on the Security Notification ATtaCHment (Snatch) ransomware gang, they added, “The Snatch ransomware gang added a new dimension to their double extortion gambit: giving cyber insurers details of how they infected victims in order to nullify coverage if those victims refuse to pay the ransom demand. Snatch claimed they would release details of how attacks against non-paying victims succeeded in the hope that insurers will decide that the incidents should not be covered by insurance.”
At this time, it is unclear how the SEC will respond to ALPHV/BlackCat’s complaint and MeridianLink’s failure to file a Form 8-K under the new cybersecurity disclosure requirements.
@CyberSleuth1 offered, “How much credibility will the SEC give to this complaint from a cybercriminal organization?”
MeridianLink did not respond to a request for comment.